The landscape of digital security is changing fast, and organizations in 2026 are feeling the pressure. With the rise in data breaches, the need for modern, reliable authentication is more urgent than ever.
This expert guide dives into enterprise auth solutions bubble, helping leaders understand how to secure their digital assets with confidence. Bubble, a top no-code platform, now makes it easier for enterprises to build custom authentication systems that scale.
Inside, you’ll find practical strategies, expert tips, and the newest trends shaping enterprise authentication. Explore each section to get the insights you need to build secure, future-ready solutions.
The State of Enterprise Authentication in 2026
Enterprise authentication is facing a pivotal moment in 2026. Organizations are grappling with more complex cyber threats, evolving compliance mandates, and increasing user expectations for frictionless access. The stakes have never been higher for those choosing the right enterprise auth solutions bubble to protect critical data and maintain trust.

Escalating Threats and Eye-Opening Statistics
In the past year alone, enterprises have seen a 40 percent surge in credential-related breaches, according to the IBM Security Report 2025. This spike is a wakeup call for decision-makers evaluating enterprise auth solutions bubble for their organizations. Attackers are increasingly sophisticated, targeting not only passwords but also exploiting weak multi-factor authentication and social engineering.
These challenges are intensified by the sheer volume of users, devices, and apps that need protection. As companies scale, so does the attack surface, making robust authentication a top boardroom priority. Regulatory bodies are also tightening requirements, especially in highly regulated sectors like finance and healthcare.
Emerging Trends: Passwordless, Biometrics, and Adaptive MFA
To combat evolving threats, enterprises are swiftly adopting cutting-edge authentication trends. Passwordless authentication is gaining traction, reducing risks associated with stolen credentials and phishing. Biometric verification, such as facial recognition and fingerprint scanning, is now mainstream in many enterprise auth solutions bubble deployments.
Adaptive multi-factor authentication (MFA) leverages real-time risk assessments to adjust security requirements based on user behavior and context. The use of AI and machine learning is transforming how organizations spot anomalies and prevent unauthorized access. For a deeper dive into these trends, IAM in 2026: Passwordless, Passkeys & AI-Driven Threats offers valuable insights into the next generation of identity and access management.
The Remote and Hybrid Work Paradigm
The rise of remote and hybrid work has fundamentally shifted authentication priorities. Employees now expect seamless, secure access from anywhere, on any device. Enterprise auth solutions bubble must accommodate flexible work models while upholding the highest security standards.
Organizations are investing in cloud-first, scalable authentication systems that can quickly adapt to changing workforce dynamics. These systems need to integrate smoothly with collaboration tools, VPNs, and mobile platforms, ensuring productivity without compromising protection.
Case Example: Fortune 500 Overhaul Post-Breach
Consider a Fortune 500 company that suffered a significant credential breach in 2025. In response, leadership launched a comprehensive overhaul of their authentication infrastructure, migrating from legacy systems to modern, cloud-based enterprise auth solutions bubble. They implemented passwordless logins, adaptive MFA, and biometric checks, dramatically reducing breach risk and restoring stakeholder confidence.
This transformation highlighted the importance of not only technology but also employee education and continuous monitoring. The company now conducts regular penetration testing and partners with leading identity providers to future-proof their security posture.
Legacy Systems vs. Modern Cloud-Based Solutions
To better understand the evolution, here is a quick comparison:
| Feature | Legacy Systems | Modern Cloud-Based Solutions |
|---|---|---|
| Authentication Types | Password-based, basic MFA | Passwordless, biometrics, adaptive MFA |
| Scalability | Limited | Highly scalable |
| Integration | Siloed, complex | API-driven, seamless |
| Compliance | Manual, fragmented | Automated, built-in |
| User Experience | Friction-heavy | Streamlined, user-centric |
Balancing security, compliance, and usability remains a challenge. However, modern enterprise auth solutions bubble are designed to strike this balance, offering robust protection without slowing down users or impeding business agility.
Why Choose Bubble for Enterprise Auth Solutions?
The demand for flexible, secure, and scalable authentication is at an all-time high. Organizations are seeking tools that streamline implementation without sacrificing security or compliance. That is where enterprise auth solutions bubble comes in, offering a modern approach to authentication challenges.

Bubble as a No-Code Platform for Enterprise Auth
Bubble has emerged as a leading no-code platform, empowering businesses to build and launch custom applications quickly. With enterprise auth solutions bubble, teams can create robust authentication workflows without writing complex code.
This approach accelerates development and reduces reliance on specialized engineering resources. Bubble’s visual editor makes it simple to map authentication flows, manage user roles, and adapt security protocols as needs evolve. As a result, companies can respond to shifting authentication requirements in real time, giving them a competitive edge.
Key Advantages for Enterprise Authentication
Why are organizations gravitating toward enterprise auth solutions bubble? The benefits are clear:
- Speed: Rapid prototyping and deployment mean faster time to market.
- Flexibility: Easily adapt authentication flows for new business requirements.
- Cost Savings: Lower development and maintenance expenses compared to traditional coding.
- Security: Built-in protocols and frequent updates ensure enterprise-grade protection.
- Integration: Seamless connections to identity providers like Okta, Azure AD, and Auth0.
Bubble also supports SSO, OAuth 2.0, SAML, and social login options, enabling diverse access scenarios. For a deeper dive into these features, check out the Bubble no-code authentication features, which details the platform’s core strengths for enterprise use.
Real-World Example and Cost Comparison
Consider a mid-sized SaaS company that needed a secure enterprise portal. By leveraging enterprise auth solutions bubble, the team launched a fully functional portal in weeks, integrating SSO and adaptive MFA.
The cost benefits were significant compared to traditional development methods. Here’s a quick comparison:
| Approach | Time to Deploy | Estimated Cost | Maintenance |
|---|---|---|---|
| Traditional Custom | 4–8 months | High | Ongoing |
| Bubble No-Code | 2–6 weeks | Moderate | Minimal |
This efficiency allowed the company to focus on growth rather than infrastructure, showcasing the strategic value of Bubble for authentication.
Limitations and Considerations
While enterprise auth solutions bubble offers many advantages, there are important considerations. Some highly specialized authentication flows may require custom plugins or external tools. Performance can be influenced by app complexity, so careful planning is essential.
Compliance with industry regulations is achievable, but it requires diligent configuration and regular audits. Teams should also consider data residency requirements and integration compatibility with legacy systems. Despite these boundaries, Bubble remains a strong choice for most enterprise authentication needs.
Step-by-Step Guide: Implementing Enterprise Auth on Bubble
Implementing enterprise auth solutions bubble is a journey that requires careful planning and execution. This step-by-step guide will walk you through the essential phases, ensuring your authentication system is both robust and scalable. Each step is designed to help you get the most out of enterprise auth solutions bubble, minimizing risk and maximizing security.
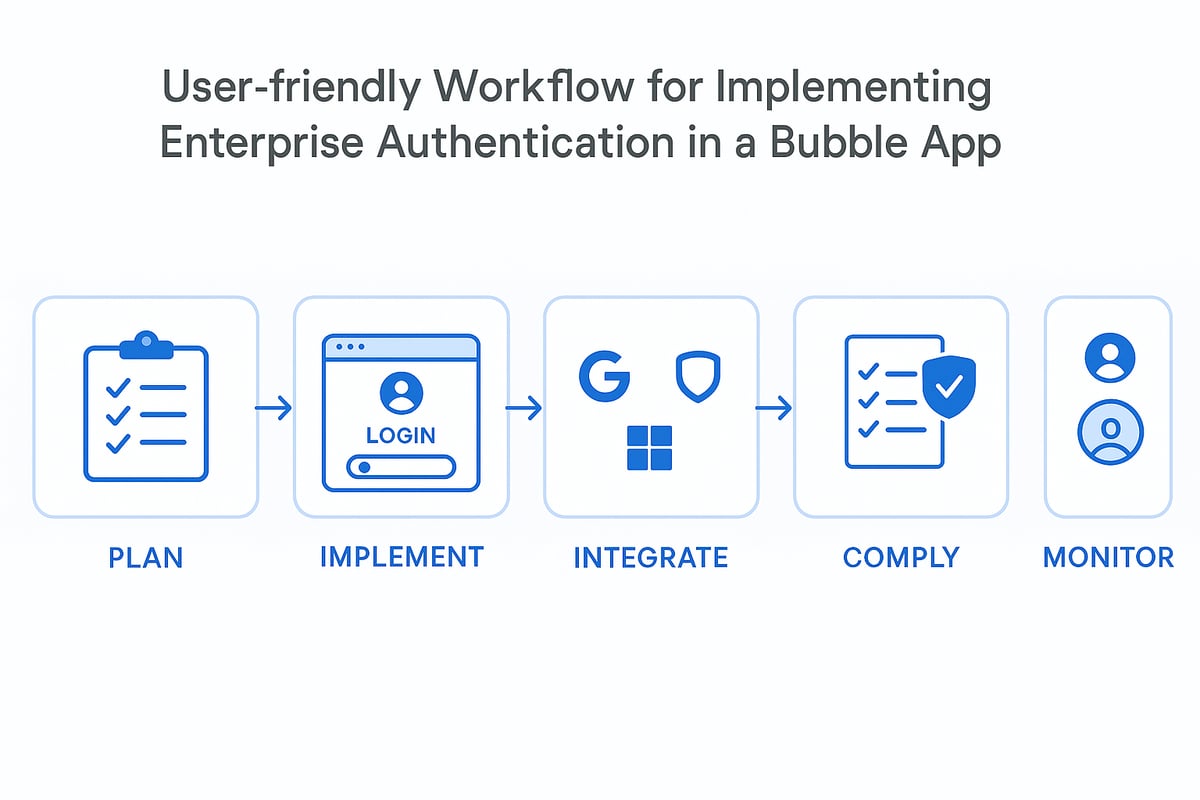
Step 1: Requirements Gathering and Planning
The foundation of any successful enterprise auth solutions bubble project is a clear understanding of your organization’s needs. Start by identifying business goals, user roles, and any compliance requirements relevant to your industry.
Map out user journeys, considering scenarios like admin access, employee onboarding, and third-party integrations. For example, a financial firm may require multi-tiered access to sensitive data, requiring precise role definitions and approval workflows.
Engage stakeholders early to align expectations and avoid costly changes later. Document these requirements to create a blueprint for your enterprise auth solutions bubble implementation.
Step 2: Configuring Bubble’s Authentication Workflows
Once you have your requirements, it’s time to set up authentication workflows in Bubble. Begin by creating user registration, login, and password management processes tailored to your enterprise needs. Bubble’s visual workflow editor allows you to configure custom logic, ensuring a seamless experience for all user types.
Enable multi-factor authentication (MFA) and passwordless options to enhance security. Customize workflows for scenarios like password resets, account lockouts, or user verification. For advanced needs, leverage plugins and API connectors to expand functionality.
If you need expert help building or customizing these workflows, consider exploring Custom Bubble app development services to ensure your enterprise auth solutions bubble meets every security and usability standard.
Testing each workflow with different user roles will help identify gaps early, ensuring a smooth rollout.
Step 3: Integrating External Identity Providers
Enterprise auth solutions bubble often require integration with external identity providers such as Okta, Azure AD, or Google Workspace. Using Bubble’s API connector, you can implement Single Sign-On (SSO) via OAuth 2.0 or SAML protocols, simplifying user access and centralizing authentication management.
Start by configuring the necessary endpoints and exchanging credentials securely. Test integrations with sandbox accounts before moving to production. Common challenges include mismatched attribute mappings or timeouts during authentication flows. Troubleshooting these issues early will save time during deployment.
Emphasize security by limiting scope and permissions to only what is necessary. Document the integration steps and keep configuration details updated, ensuring the enterprise auth solutions bubble remains adaptable to future changes.
Step 4: Enhancing Security and Compliance
Security and compliance are at the heart of any enterprise auth solutions bubble implementation. Enforce strong password policies, set session timeouts, and enable audit logging to monitor user activity.
Implement activity monitoring to detect suspicious behavior and respond proactively. Ensure your Bubble app aligns with regulations like GDPR, CCPA, and SOC 2 by encrypting sensitive data and maintaining detailed records of user access.
Schedule regular reviews of security settings and compliance checklists. Train your team on best practices, such as least-privilege access and incident response protocols. Keeping your enterprise auth solutions bubble compliant will help you avoid costly penalties and reputational risks.
Step 5: Testing, Deployment, and Maintenance
Thorough testing is vital for a successful enterprise auth solutions bubble rollout. Conduct penetration testing and vulnerability assessments to uncover potential weaknesses. Use staging environments to simulate real-world scenarios, ensuring all authentication flows function as intended.
During deployment, follow best practices like phased rollouts and user education to minimize disruption. After launch, set up monitoring tools to track system health, user activity, and potential threats. Schedule regular updates to address security patches and evolving compliance needs.
Provide ongoing support for users, offering clear documentation and responsive help channels. By maintaining your enterprise auth solutions bubble with these strategies, you ensure resilience, scalability, and security for the long term.
Integration Strategies: Bubble with Enterprise Systems
In 2026, seamless integration is the backbone of successful enterprise auth solutions bubble projects. Modern organizations demand that authentication systems connect effortlessly with critical business apps, so robust integration strategies are essential for scalability and security.

Connecting Bubble to Enterprise Systems: CRM, ERP, HRIS, and APIs
Enterprise auth solutions bubble projects often require integration with core systems like CRM (Salesforce), ERP (SAP), and HRIS (Workday). Bubble’s integration flexibility allows organizations to centralize identity management while maintaining efficient workflows.
Here’s a table summarizing common enterprise integrations:
| Integration Type | Purpose | Key Considerations |
|---|---|---|
| CRM | Sync user data | Data mapping, permissions |
| ERP | Access control | Compliance, audit trails |
| HRIS | User onboarding | Real-time updates, privacy |
| Custom APIs | Unique workflows | Rate limits, error handling |
By connecting these systems, enterprises can automate user provisioning and ensure consistent access controls across platforms.
Leveraging the API Connector and Identity Synchronization
One of the standout features in enterprise auth solutions bubble is the API Connector. This tool enables secure, low-code integrations with external services. For syncing user identities, protocols like SCIM and LDAP are vital.
A sample API call for user sync might look like:
POST /scim/v2/Users
{
"userName": "jane.doe@company.com",
"name": { "givenName": "Jane", "familyName": "Doe" },
"active": true
}
Using SCIM, Bubble apps can synchronize users with directories like Azure AD or Okta, ensuring that access rights are always up to date. This reduces manual intervention and the risk of orphaned accounts.
Real-World Example: Integrating with Salesforce and Microsoft Dynamics
Consider a global manufacturer that adopted enterprise auth solutions bubble to streamline access across Salesforce and Microsoft Dynamics. The company used Bubble’s API Connector to authenticate users, fetch permissions, and synchronize CRM data in real-time.
During implementation, the team mapped user roles between systems to maintain least-privilege access. They also set up automated workflows for onboarding and de-provisioning, triggered by HRIS events. This approach eliminated redundant logins and improved user experience, while supporting compliance needs.
Security, Data Residency, and Best Practices
Security is non-negotiable in enterprise auth solutions bubble integrations. When linking to third-party systems, always use encrypted channels (HTTPS/TLS) and enforce strict authentication. Consider data residency requirements, especially for cross-border operations, to comply with regulations like GDPR.
To further strengthen your integration strategy, follow these best practices:
- Monitor API usage and set rate limits.
- Implement robust error handling for failed syncs.
- Schedule regular audits of access logs.
- Document integration points for compliance reviews.
For more insights on secure, scalable app development and integration, see Enterprise-level application development.
By aligning integration strategies with security and compliance priorities, organizations can unlock the full potential of enterprise auth solutions bubble. This ensures digital assets stay protected, user productivity remains high, and your authentication framework is ready for the future.
Compliance, Security, and Best Practices for 2026
In 2026, compliance is no longer a checkbox exercise. Regulatory frameworks like GDPR, CCPA, and HIPAA now set the bar for how organizations handle data. Global standards continue to evolve, making it crucial for decision-makers to stay ahead of requirements. The enterprise auth solutions bubble landscape demands a proactive approach, as regulations increasingly focus on user consent, data minimization, and breach notification.
Navigating the Regulatory Landscape
Modern enterprises face a maze of compliance obligations. GDPR and CCPA emphasize user privacy and transparency, while HIPAA governs healthcare data. Emerging global standards require adaptable solutions. According to the Enterprise CIAM Migration Patterns Report 2026, organizations migrating to advanced authentication platforms saw significant improvements in both compliance and breach reduction.
The enterprise auth solutions bubble approach is well-suited for rapid regulatory adaptation. Bubble’s flexibility lets teams quickly update consent mechanisms, privacy policies, and user rights management, supporting compliance in dynamic legal environments.
Security Frameworks for Bubble Applications
Adopting industry frameworks is fundamental for robust security. Zero Trust, NIST, and ISO 27001 provide a blueprint for controlling access and managing risk. With enterprise auth solutions bubble, admins can implement least-privilege access and role-based permissions, ensuring users only see what they need.
Best practices include:
- Enforcing strong password policies and multi-factor authentication
- Segregating duties among admin roles
- Regularly reviewing and updating user permissions
Bubble’s extensibility allows integration of these controls, helping enterprises align with the latest security standards.
Data Protection, Auditing, and Compliance in Action
Protecting sensitive data is at the core of every compliance strategy. Encryption at rest and in transit is a non-negotiable feature of enterprise auth solutions bubble. Bubble supports secure data practices, making it easier to implement end-to-end encryption.
Routine audits and penetration testing are essential. A healthcare provider using Bubble achieved HIPAA compliance by combining real-time activity logging, automated alerts, and detailed incident response plans. Regular documentation and evidence collection ensured smooth compliance audits, demonstrating the platform’s readiness for regulatory scrutiny.
Avoiding Pitfalls and Ensuring Ongoing Compliance
Common pitfalls include overlooking documentation, failing to update policies, or neglecting routine security reviews. To avoid these issues, organizations should:
- Maintain clear records of access and changes
- Schedule regular internal audits
- Stay informed on new regulations
With enterprise auth solutions bubble, continuous monitoring and prompt updates help close compliance gaps. By embedding best practices into daily operations, teams can confidently meet the demands of 2026 and beyond.
Future-Proofing Enterprise Auth: Trends and Innovations
The pace of change in enterprise authentication is accelerating, and organizations must look beyond today’s standards to stay secure. As digital threats evolve, so must the strategies behind enterprise auth solutions bubble. To remain competitive and compliant in 2026 and beyond, forward-thinking leaders are already preparing for what’s next.
The Decentralized Identity Revolution
One of the most significant innovations shaping enterprise auth solutions bubble is the rise of decentralized identity (DID). Unlike traditional models that rely on centralized databases, DID empowers users to control their digital credentials. Verifiable credentials make it easier for organizations to validate identities securely, reducing the risk of large-scale breaches.
Blockchain-based identity solutions are gaining traction, offering tamper-resistant records and privacy by design. Early adopters are leveraging these technologies to streamline onboarding, simplify compliance, and enhance user experiences.
AI, Biometrics, and Regulatory Shifts
Artificial intelligence is transforming how enterprise auth solutions bubble detect and respond to threats. AI-driven adaptive authentication analyzes behavioral patterns in real time, flagging anomalies and preventing unauthorized access. Behavioral biometrics, such as typing rhythm and mouse movement, add another layer of security.
Regulatory changes are also influencing the future of authentication. New global standards are emerging, requiring organizations to ensure transparency, user consent, and robust data protection. Staying compliant means continuously updating authentication protocols and investing in staff training.
Quantum-Safe Authentication and Bubble’s Roadmap
Quantum computing is on the horizon, and its potential to break current encryption methods has major implications for enterprise auth solutions bubble. Forward-looking organizations are already exploring quantum-safe cryptography and biometric authentication. For an in-depth look at the latest research, see Quantum Secure Biometric Authentication in Decentralised Systems.
Bubble’s roadmap includes enhancements to support advanced authentication, with a focus on extensible APIs, improved SSO support, and integration with decentralized identity providers. These updates will help organizations future-proof their authentication systems as new threats and technologies emerge.
Staying Ahead: Best Practices for 2026 and Beyond
To keep enterprise auth solutions bubble resilient, decision-makers should:
- Monitor emerging technologies like DIDs, AI, and quantum-safe encryption.
- Regularly review and update authentication workflows.
- Invest in robust compliance and user privacy strategies.
- Collaborate with vendors committed to security innovation.
- Encourage a culture of security awareness across all teams.
By taking these proactive steps, organizations can ensure their authentication strategies are secure, scalable, and ready for whatever the future holds.
As we’ve explored, navigating the future of enterprise authentication means balancing security, scalability, and usability—all while keeping up with rapid changes in tech and regulation. If you’re thinking about bringing secure, no code solutions like Bubble into your organization or want expert advice tailored to your unique needs, why not chat with someone who’s been there? You don’t have to figure this out alone—we’re here to help you design and launch authentication systems that truly work for your team. Talk to a No Code Strategist and let’s make your next project a success together.




About Big House
Big House is committed to 1) developing robust internal tools for enterprises, and 2) crafting minimum viable products (MVPs) that help startups and entrepreneurs bring their visions to life.
If you'd like to explore how we can build technology for you, get in touch. We'd be excited to discuss what you have in mind.
Other Articles
Master rep lit python with our 2025 guide Explore hands on projects career paths and advanced techniques to boost your coding skills and stay future ready
Discover the top 7 enterprise integration platforms no code for 2026 Compare features pricing and benefits to streamline automation and boost business agility
Discover everything beginners need to know about software designers in 2025. Learn roles, skills, tools, and career tips to start your design journey today.